|---Module:text|Size:Small---| In complex, microservices-based environments, managing access is complex. Celfocus helps CSPs ensure security without slowing their digital transformation journeys
As digital systems grow more complex and interconnected, access control has become a fundamental pillar of cybersecurity. Organisations must ensure that the right people have the right access, at the right time, while minimising risk.
Two commonly used models are Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC). While both aim to manage permissions effectively, they differ significantly in approach and flexibility. Understanding their strengths, limitations, and ideal use cases is crucial to choosing the right model for any organisation.
So, what is RBAC (Role-Based Access Control)?
RBAC is a widely adopted access control model that assigns permissions based on roles within an organisation. A role is a collection of permissions that correspond to job functions (e.g., HR Manager, Sales Executive, System Administrator). Users are assigned to roles, and through those roles, they inherit specific access rights.
Advantages of RBAC:
- Simplicity and clarity: Roles and their permissions are explicitly defined, making the system easy to manage
- Least privilege enforcement: Users only get the access required for their role, reducing security risks
- Scalability: Works well where job functions are stable and clearly separated
Example: An HR Manager role might include access to employee records but not financial systems. Any user assigned to this role automatically receives these permissions.
Now… what is ABAC (Attribute-Based Access Control)?
ABAC takes a more dynamic and granular approach by assigning permissions based on attributes rather than fixed roles. These attributes can relate to:
- The user (e.g., department, clearance level)
- The resource (e.g., sensitivity level, data type)
- The environment (e.g., time of access, location, device used)
ABAC policies evaluate these attributes in real time to determine whether access should be granted or denied, allowing organisations to adapt to a variety of conditions and contexts.
Advantages of ABAC:
- Flexibility: Can handle complex scenarios and conditional logic
- Context-aware: Permissions can adapt based on when, where, and how access is requested
- Policy-based: Access is controlled by logic defined in policies, not rigid roles
Example: A user from the Finance department can access budget reports only if they are on a corporate network and during business hours.
|---Module:text|Size:Small---|
What is the Best Approach for CSPs?
For Communication Service Providers (CSPs), there’s usually a need to modernise and strengthen how users and systems are granted access across a distributed, cloud-native architecture. To do this securely and efficiently, CSPs need to evaluate different Authorisation Architecture options, particularly around implementing ABAC.
At Celfocus, based on our experience with similar projects in the telecom sector, we present several approaches to help CSPs balance security, performance, and project timelines.
In a complex, microservices-based environment, managing who can access what – and under which conditions – becomes very demanding. CSPs must meet strict security requirements without delaying their digital transformation goals.
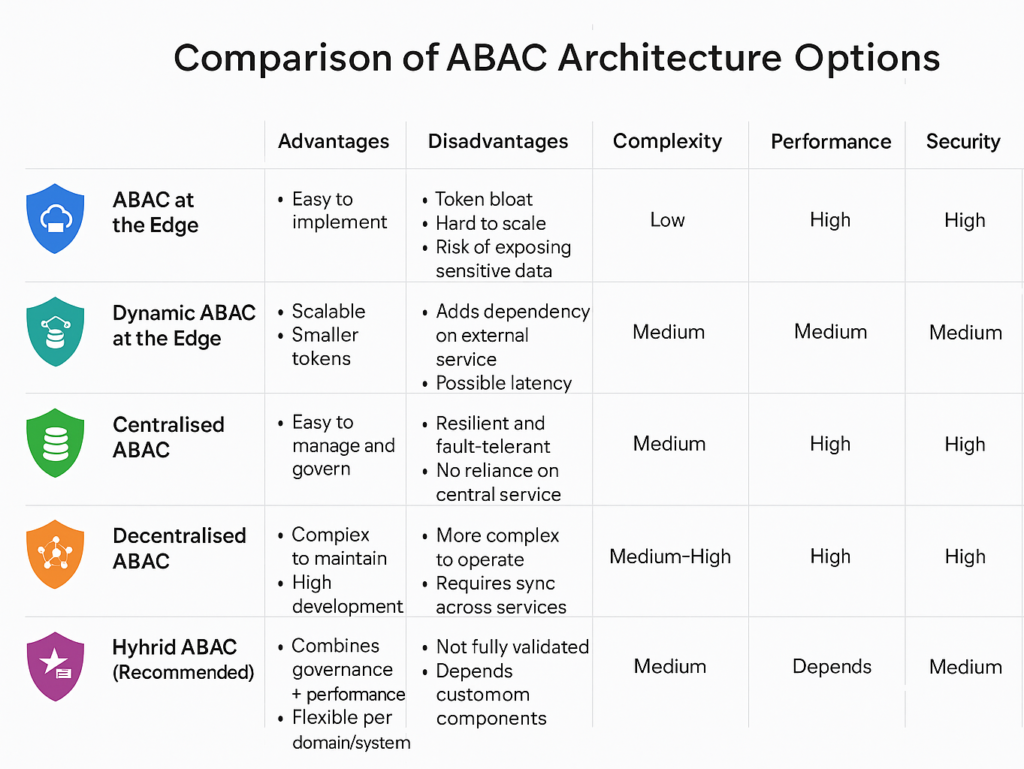
Key Implementation Options:
1. ABAC at the Edge (API Gateway only)
- Uses access tokens to validate permissions at the gateway level
- Easy to implement and centralised
- Limited flexibility, larger tokens, possible exposure of sensitive data
2. Dynamic ABAC at the Edge
- Improves the previous model by querying permissions dynamically from an external service
- More scalable, lighter tokens, better data protection
- Adds dependency on external services and increases complexity
3. Centralised ABAC
- Policies are defined and managed centrally, and access decisions are made by a central server
- Consistent and easy to govern
- Risk of single point of failure and higher latency
4. Decentralised ABAC
- Policies are embedded in each application or service
- Highly resilient and scalable
- Increases development and operational complexity
5. Hybrid ABAC (Celfocus’s Recommended Approach)
- Combines centralised policy management with decentralised decision-making
- Balances control and performance, reduces latency
- More complex to operate, requires synchronisation across systems
|---Module:image|Size:Small---|
|---Module:text|Size:Small---|
Conclusion
As mentioned before in this article, there’s no one-size-fits-all solution.
Both RBAC and ABAC offer valuable benefits, and the right choice depends entirely on each organisation’s specific needs, infrastructure, and strategic priorities.
While Celfocus recommends a more ABAC-oriented approach for CSPs – particularly a hybrid model that combines centralised policy management with decentralised decision-making – this is not a blanket solution. In some cases, especially where roles and responsibilities are stable and well-defined, RBAC may be the most effective and efficient model.
Ultimately, a careful, case-by-case assessment is essential. Whether the choice leans towards RBAC, ABAC, or a hybrid model, Celfocus advises to align the access control strategy with the organisation’s technology stack, team capacity, and transformation goals.