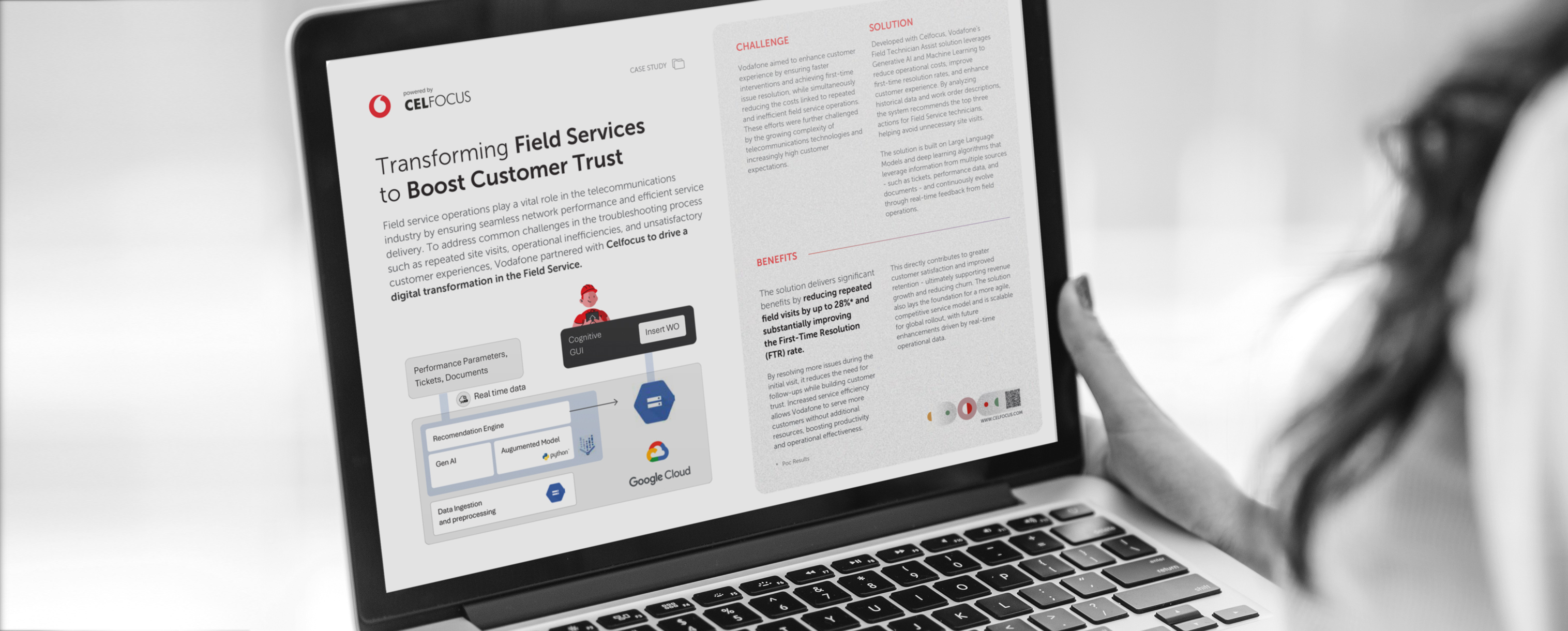
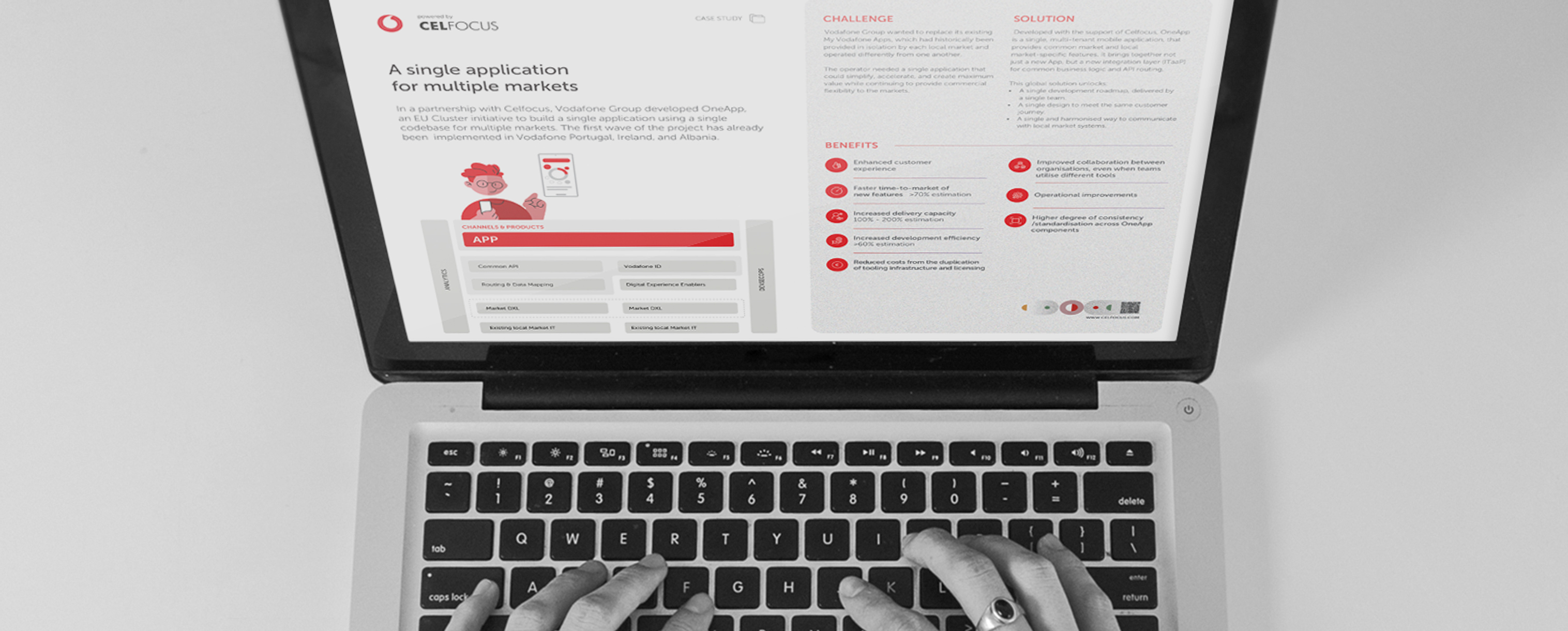
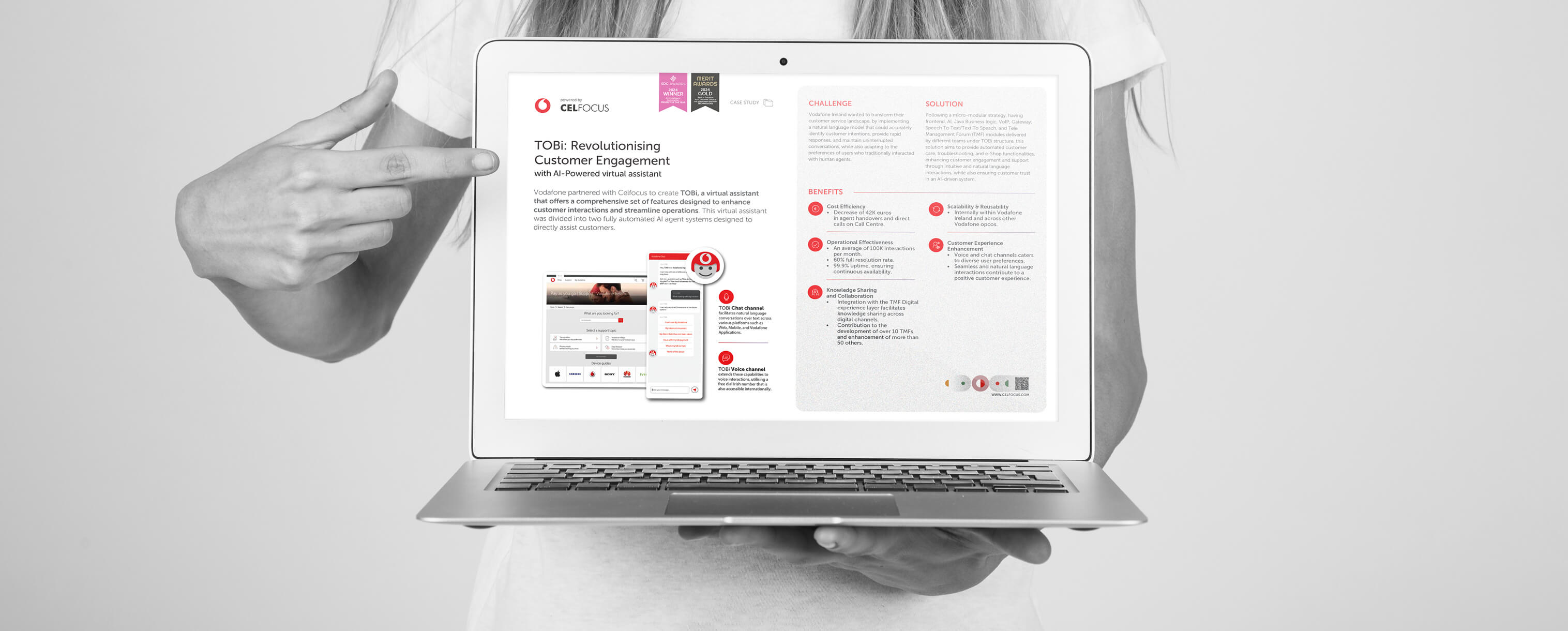
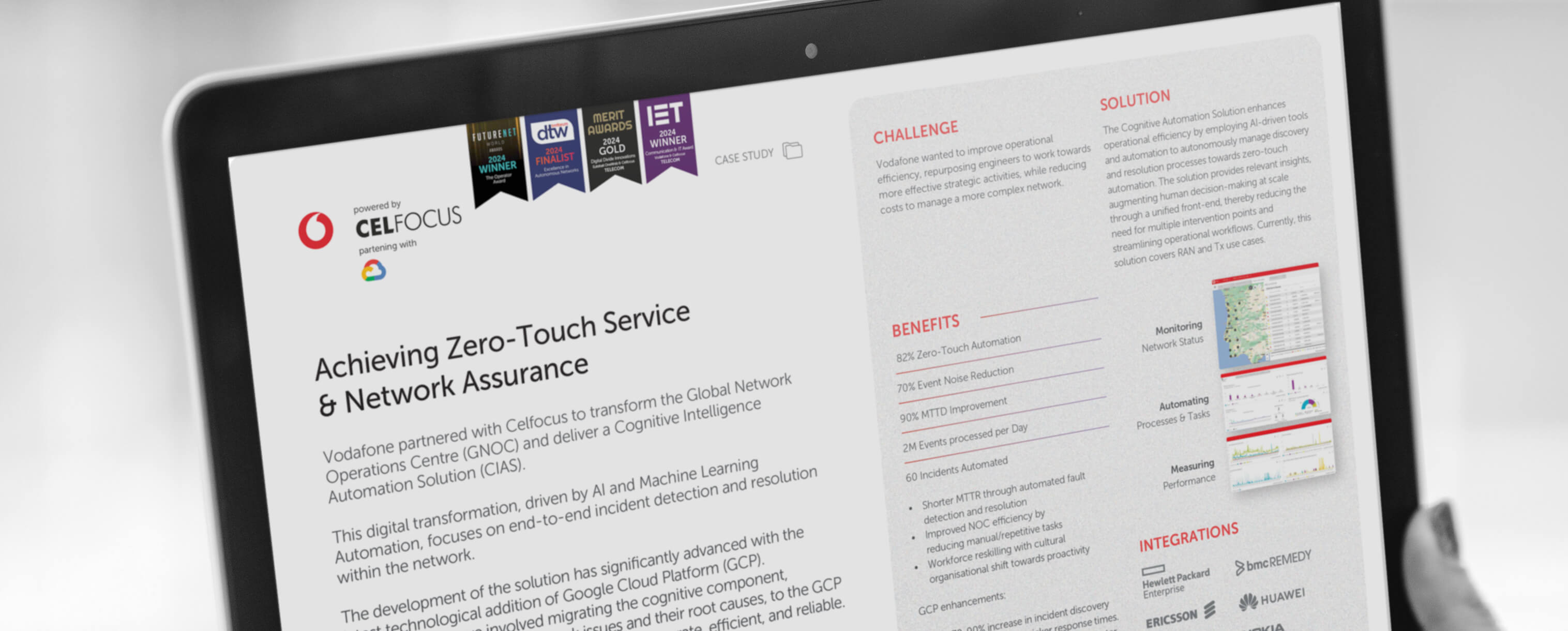
|---Module:text|Size:Small---|
Here’s the full opinion article transcription:
In June 2025, the cybersecurity community was shaken by a discovery of unprecedented proportions. Over 16 billion compromised credentials were made public, the result of a type of malicious software that, operating undetected for years, harvested confidential data silently and persistently. Until then, the largest known breach involved SIM card data in Indonesia, affecting around 1.3 billion records.
This latest case far surpasses that, becoming the largest credential leak ever identified. But to call it an "incident" is to understate the severity of what has occurred. It was a seismic event, a stark warning about the fragility of the digital defences we rely on. In a context where threats evolve faster than systems can respond, this case exposed more than isolated flaws. It laid bare a structural deficiency in how we approach digital security. Being reactive is no longer enough and hasn’t been for some time.
What is most alarming is not the scale, but the method. Rather than a direct attack on a major platform, the data was drained off quietly and continuously from devices infected with infostealer malware. This type of malicious software is typically installed, often unknowingly, on users’ personal or corporate devices, whether employees or end customers, most commonly via phishing campaigns, compromised downloads, or malicious attachments. Its purpose is to automatically extract credentials, cookies, and other sensitive information. Usernames, passwords, form data, all silently captured, turning computers and smartphones into constant sources of data exfiltration.
What sets this threat apart is its persistence, decentralisation, and difficulty of detection. It is not a traditional attack that is quickly identified, mitigated, and forgotten. It is a prolonged infiltration, with cumulative impact. And the results are now clear: sensitive data is circulating on criminal networks, ready to be exploited to access accounts, deceive users, or compromise entire organisations.
This is far from an isolated event. It highlights a deeper issue: our collective approach to digital security is outdated.
Most individuals still rely on weak, reused passwords that are easily guessed or phished. Even with the widespread adoption of multi-factor authentication (MFA), attackers continue to adapt, using techniques such as social engineering and other forms of circumvention.
Organisations, for their part, remain trapped in a reactive cycle, only investing after incidents occur, only updating policies after damage is done. This pattern reinforces vulnerability, while threat actors become faster, more organised, and increasingly sophisticated.
The impact goes beyond technical risk. Digital trust, the foundation of customer relationships, reputation, and brand value, is at stake. People expect their data to be protected. When that trust is broken, regaining it is anything but easy.
The answer does not lie in piling on more controls or alerts. We need a fundamentally different approach. Solutions that are designed from the ground up with security as a priority, not as an afterthought. That means adopting zero-trust architecture, threat modelling, authentication methods that secure without obstructing, and, above all, a strategic mindset for security.
More than a technological shift, this requires a cultural transformation. Security must be embedded across teams, processes, and leadership decisions. It is no longer a purely technical issue; it is a condition for the sustainability of our systems and services.
The future demands more than fast reactions. It demands foresight, integration, and long-term strategy. This breach must not be just another ignored warning. It should be a turning point where digital security ceases to be a reaction and becomes the foundation of everything we build. Only then can we rebuild trust and ensure that we are truly prepared for what lies ahead.
Cybersecurity is no longer optional; it is essential for the sustainability of our systems, and for the trust that underpins them.